Cybercrime is an ever-present threat to business, especially given how reliant companies are on their IT networks. However, fewer than 1% of the people who commit cyberattacks have ever experienced enforcement action taken against them. That shows that this type of crime is not to be ignored, and it is up to businesses to reduce the chances of it happening to them. One effective way of achieving that is to commit to training employees on cybersecurity.
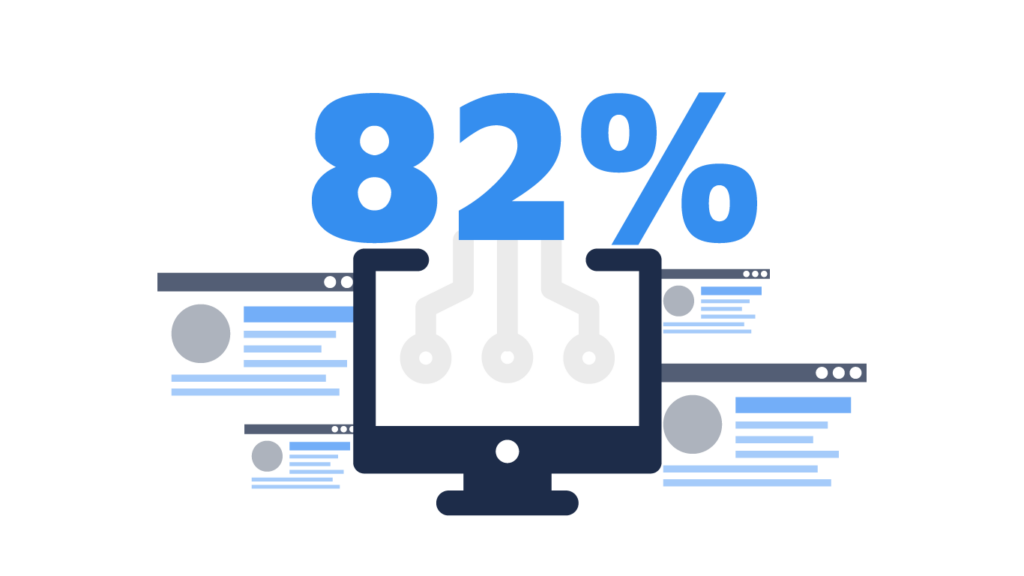
With 82% of data breaches involving human error of some kind, arming your employees with the tools they need to prevent attacks on your network and work safely is an essential activity in your IT strategy. And this is even more important when you have remote employees to consider, too.
Why is cybersecurity training important in a remote work setting?
Hybrid and fully remote working are here to stay and, as well as providing convenience and flexibility to your employees, it also brings a potential security headache for IT professionals. Some of the increased risks of remote working include:
| Threat | Explanation |
| Employees using their own devices | Dedicated work devices, issued by IT, will have the full range of security features and can be monitored to ensure the software is up to date. Employees’ own devices might be running old versions of software and have no virus protection or two-factor authentication. |
| Unsecured networks | Home networks are less secure than enterprise solutions. Public WiFi, if employees work from coffee shops for example, is even more of a risk. |
| Storage devices | There is a chance of devices used for storing sensitive information being stolen or lost when an employee works in a remote location, |
| Shadow IT | At home, employees are more likely to use their own, unapproved solutions for work, such as SaaS apps and personal email. This can lead to cyberattacks through vulnerabilities and also issues with maintaining data protection. |
7 steps to training employees on cybersecurity
1. Make the security threats easy to understand
It is important to remember that employees might not understand the threats at hand. Individual employees often don’t think about cybersecurity when they are carrying out their duties. In fact, measures like coming up with strong passwords and using a VPN to disguise their IP address when working on unprotected networks are an inconvenience to them when it comes to completing their tasks.
This is why you need to make sure that your security awareness training is framed in simple language, avoiding technical jargon that could alienate or disengage regular workers. Relate the threats to how they affect the employee and their devices instead of talking about the whole network. This will help them understand their role in keeping the company safe.
2. Focus on behavior, not just technical skills
The technical skills of your employees are important when it comes to cybersecurity, but changing their behavior is what is going to really help you avoid attacks.
The types of behavior you need to encourage in employees include spotting potential threats and refraining from interacting with them. Knowing how to use a VPN is one thing, but it can almost make employees blase, as if they feel they don’t have to worry because they have a safety net. Instilling in them the importance of being alert to threats is key to the success of your cybersecurity training – it leads them to put security first in everything they do.
Additionally, encouraging a speak-up culture in which employees feel confident in reporting breaches immediately, without fear of reprisals, is important, too.
3. Implement a remote work IT security policy
A remote work IT security policy is a handy document that collates all of the expectations and requirements for employees in one place. They can reference it at any time, whenever they are unsure of the best course of action.
The policy spells out your standards for passwords, shadow IT, and other issues that can cause remote workers to accidentally compromise your security protocols. In addition, it tells employees what to do in the event of a breach and reminds them of the sanctions for purposefully ignoring the best practices in place for cybersecurity.
4. Pair security training with security technology
Relying solely on employees to get things right all of the time can be a little unfair. So, complement your cybersecurity awareness training with technology that works behind the scenes to keep the business safe.
For example, don’t just ask employees to create strong passwords; add a requirement during the process of creating a password that does not allow simple or common passwords to be used.
Regularly auditing and improving your remote access controls can also limit the damage of breaches to the company. Another way to boost the effectiveness of your training is to add automation to improve the efficiency of reporting suspect emails. In that training, you should explain why these measures are in place and how they help.
5. Include cybersecurity in onboarding
Maintaining a safe cyber environment is as important as any other element of the traditional onboarding process, and it should be treated as such. By adding your policy into the welcome package, you ensure that employees envelop it into their working life from the start and don’t have to change their behavior after a few weeks when you finally introduce it.
Protecting the business is paramount. So, understanding how best to avoid attacks and data breaches is key for any employee.
6. Make it an ongoing process and assess employee knowledge
The best way to keep cybersecurity at the front of people’s minds, especially if they work remotely and do not have regular contact with IT, is to make security training an ongoing process. Book regular training sessions to maintain interest and to update employees on any developments.
You can also assess their knowledge to understand which areas of security you need to concentrate on with your training efforts. Ongoing training also provides a regular check-in that makes remote workers feel part of the team and reminds them of their value within the organization.
7. Run cybersecurity fire drills
Once you have a plan in place and procedures designated for responding to a cyberattack, you can run a cybersecurity fire drill. This is a practice run to ensure that employees know what to do in the event of a breach.
By simulating what happens when an attack takes place, you can focus people’s minds on the actions that they will need to take in case it happens in real life. Make sure all employees are involved, from senior leadership downward, and follow up with areas for improvement that become obvious from the drill.
What to include in cybersecurity training
The following items should all be included in your training:
Password security
53% of IT leaders say that their company had experienced a data breach as a result of employees mismanaging their credentials. There is no doubt that password security should be high on your list of priorities. Instilling the need for strong passwords and 2FA or multifactor authentication (MFA) is essential.

One side effect of remote employees working on personal devices or using personal email is the increased chance of a phishing attack. Understanding how to spot phishing and other social engineering attacks is important for preventing malicious cyber actors from gaining access to sensitive business information.
Responsibility for company data
Employees should understand both the moral and legal implications of mishandling company data and personal information. You must explain why handling such data in an unsecured manner could have serious ramifications for the organization.
Remote document management
The temptation for remote teams is to revert to using shadow IT solutions for managing documents. Using commercial B2C options might be familiar, but the security implications should be grave. In your training, explain the concerns and demonstrate the IT-approved solution.

Broadening that scope, you should be clear on your shadow IT policy in general. Explain the potential costs to the business of using unauthorized programs, and show employees how to access the sanctioned options. You can also use this as a feedback session to understand what functionality employees believe is missing so you can provide an approved program to bridge that gap.
FAQs
How does remote work affect data breaches?
Remote work can increase the chances of data breaches from employees using their own devices, unauthorized programs, unsecured networks, and other practices. It also occurs outside the vision of IT, which means that issues may fester before anyone notices.
How often should you train employees on cybersecurity?
Employee training on cybersecurity should be an ongoing process, as it is a shifting landscape. It also keeps the key messages in the minds of employees, reinforcing the desired behaviors. Make sure you train workers every few months at least.
What are the benefits of a zero-trust policy?
A zero-trust policy, whereby anyone connecting to the network is treated as a potential threat, is a secure way of running your IT policy. It allows for better monitoring and for keeping track of exactly what is going on in the business – from the weakest link to the strongest.
Conclusion
Training employees on cybersecurity is your best chance of reducing breaches and attacks from external forces on your network. By helping your remote staff understand the behaviors that lead to security issues, you can guide them toward best practices. This means being more cautious of potential phishing attempts, staying secure when working on public networks, and avoiding the use of shadow IT.
Vaultry helps you monitor all mobile devices connected to your network to find any unauthorized programs or devices. It is simple to use but provides timely information on potential cyber threats that allows you to remove them before they cause damage. Get started with Vaultry today.




