Cybersecurity Ventures predicts the cost of cybercrime will pass $8 trillion during 2023 and could even grow to $10.5 trillion by 2025. This shows the importance of a dedicated and robust cybersecurity policy within your organization, and the way to measure the success of your efforts is to track a variety of relevant metrics. This article provides a list of cybersecurity KPI examples that you can monitor to embolden your network security.
What are cybersecurity KPIs?
Cybersecurity KPIs are key performance indicators that businesses can use to measure the effectiveness of their cybersecurity efforts. These metrics help businesses track and evaluate the success of their cybersecurity strategies and identify areas where improvements can be made.
Why are cybersecurity metrics important?
Cybersecurity is a continually shifting environment. You cannot simply put in procedures and policies to prevent cyberattacks and then forget about them and hope that they will continue to work. You have to track the effectiveness of your cybersecurity efforts and adjust accordingly if they underperform. The way to do this is to identify and monitor the most important cybersecurity metrics.
Without being able to gain a tangible insight on whether the actions you take are working, you cannot make informed decisions on cybersecurity, and you could leave your organization open to vulnerabilities.
The key performance indicators (KPIs) you track provide a fuller picture of the state of cybersecurity within your business, helping you identify and mitigate risks more easily.
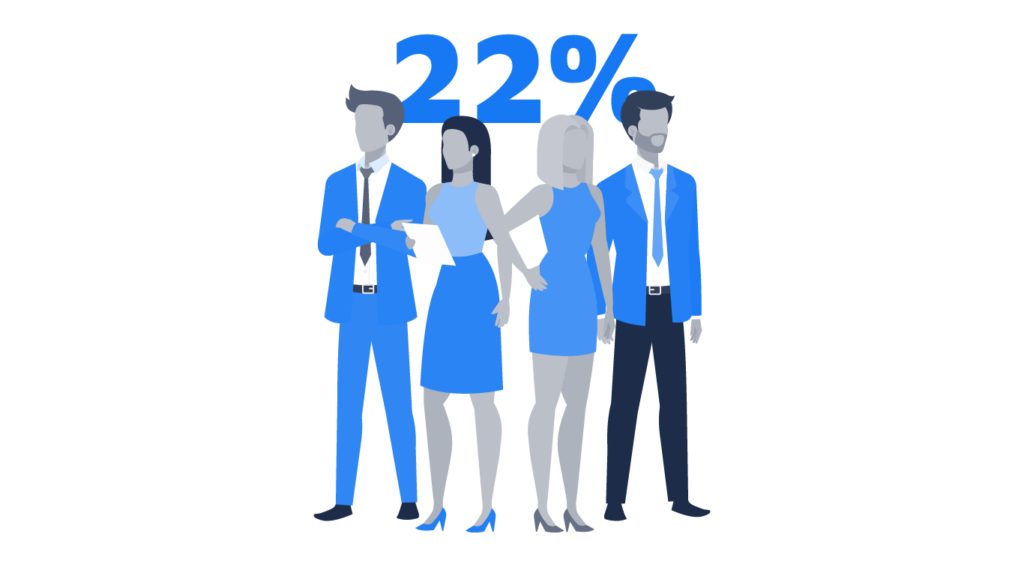
PwC found that only 22% of chief executives believed they received sufficiently comprehensive risk exposure data to inform effective decisions. Tracking the right cybersecurity KPIs better informs senior leaders over their efforts to prevent cybercrime.
How to choose cybersecurity KPIs
You need to choose KPIs that are easy to explain to all stakeholders within the organization. IT departments can sometimes choose very technical metrics that non-specialists might not understand. This makes it difficult for them to use your KPIs effectively to guide decision-making. Think of a more universally accessible alternative that makes it easy for all stakeholders to track your cybersecurity protections.
Your KPIs also need to reflect the unique situation of your business. The important aspects of IT security for you will be different from those of other companies and, in many cases, even your peers. Take into account your sector, the regulations that apply to the business, your internal best practices, current and future threats, your risk appetite, and other factors so that you can choose KPIs that will be valuable to your business for tracking cybersecurity presence.
The 10 must-track cybersecurity KPIs + examples
1. Unidentified devices on internal networks
Being able to account for all the devices connected to your network is essential for cybersecurity. For authorized devices, you can ensure that there are the necessary protections and security measures in place to minimize the chance of cyberattacks.
When people connect their own devices or other unidentified hardware to your network, you have no oversight over the protections in place, and it can create a vulnerability.
Using Vaultry, you can scan your network to find any unauthorized access points, disconnecting them before they can cause a problem. Track the number of unidentified devices over time. This enables you to understand whether you need to commit more time to training employees on the use of their own devices or implement sanctions for those who continue to log on with unidentified devices.

2. Security incidents
Looking at the number and nature of security incidents allows you to figure out how they are happening and how to prevent them in the future. Your cybersecurity systems are tasked with minimizing criminals accessing your systems, so this KPI is incredibly important for shaping your policies.
Look at the number of successful security breaches and whether they were resolved. Track the time it took to resolve them, too. Of course, if your procedures are working effectively, there will be fewer incidents as time goes on, and you will be quicker at restoring order. However, if these KPIs track in the other direction, you know that you have to reconsider your approach.
3. Number of known vulnerabilities within internal systems
Known vulnerabilities are those weaknesses in software and hardware that cybercriminals have exposed and can use to access your network and cause problems. With companies running a multitude of programs across a range of devices, it can be difficult to close all of these backdoors manually.
By carrying out a vulnerability scan, you can understand how many weaknesses there are in your systems, and you can begin to take action, prioritizing those that pose the most immediate threat.
This metric helps you understand how many devices and users are affected by each vulnerability, and that can help with understanding which vulnerability to counter first. It can also help you formulate a policy to help you effectively manage software updates and patches for your users, rather than relying on them to ensure they are running the most recent versions of the programs they use.
4. Mean-time metrics and KPIs
These metrics measure the speed with which you detect and address threats, making them essential for understanding if you are heading in the right direction with your cybersecurity policies. The main types of mean-time metrics are:
| Metric | Explanation |
| Mean time to detect (MTTD) | The average time it takes from the threat to enter the network to it being noticed by the IT department. If the average does not come down over time, you need to look into your monitoring systems. |
| Mean time to contain (MTTC) | How long it takes from detection to shutting down the threat so it cannot spread further within your system. |
| Mean time to resolve (MTTR) | How long it takes until you nullify a threat that has entered your system and stop it from causing damage. |
| Mean time between failures (MTBF) | The longer the time between successful attacks on your network, the better your preventative measures are working. |
| Mean time to acknowledge (MTTA) | This is the average time between someone making a report of a violation and the IT team beginning to work on resolving it. The shorter the response time, the better. |
| Mean time to recovery (MTTR) | The mean time to recovery measures the entire span from the moment of the attack to the time when your systems are back to normal and running as they should again. |
5. First-party security ratings
Security ratings agencies rank organizations based on a range of criteria related to their cybersecurity performance. They provide a score that helps organizations understand where they stand against their peers.
By using these ratings as part of your KPIs, you can communicate your progress more easily to stakeholders who might not understand some of the more technical metrics. These simple rankings provide a score that you can track to make sure you are making progress in your efforts to protect the business from cybercriminals.
6. Third-party risk
If you deal with third parties and share access to your network, then you do not only have to worry about your own cybersecurity; you also have to ensure that third-party vendors do not create another vulnerability.
You should carry out risk assessments on all third parties with access to your network and monitor those metrics to ensure you are not taking on risk above and beyond your company’s appetite.
Consider how many vendors you have and the percentage of which you would categorize as high risk. If that number rises above an acceptable limit, you will have to formulate a strategy to mitigate the risk at hand.
7. Phishing test success rate
Sending out fake phishing emails to test your employees’ awareness of these threats is an important step to correctly pitching your security awareness initiatives. If staff members generally ignore or report the phishing attempt, it shows that you are on the right track with your cybersecurity training.
However, if your tests show that there are still significant numbers of employees sharing their details in this way, you know that you need to double down on helping them understand the threats involved with not checking the veracity of messages that they receive and interact with.
This test also helps you track the number of phishing emails that your system blocks. Track this number and, if more and more get through, look into how you can tweak the settings to keep your employees and the company safe.
8. Patch time lag
When users fail to update their software, it can lead to vulnerabilities that criminals can exploit. Ideally, any time a software provider releases a patch, you would want that to be applied to all relevant devices in your network.
However, some users may have turned off automatic updates and not seen the patch or understood the reasons that they should install it on their device.
If the time between release and installation is too long, your network is open to attack, and you must think about training users, mandating automatic updates, or putting into action another remedial action.
9. Vulnerability scanning frequency
The more you scan your network for vulnerabilities, the more likely you are to uncover issues that you need to fix. The longer you take between scans, the more likely it is that cybercriminals can use them to attack you.
Using Vaultry helps you maintain a continual scanning of your systems to detect key generators, torrented software, cracked software, and unapproved freemium programs that pose a serious risk to your company.
10. Employee security awareness
Your employees are the frontline in your battle against cybersecurity. This means you should monitor how much they know about cybersecurity and their part in the battle against criminal activity.
You could issue a questionnaire to assess their understanding of your cybersecurity policies. Another way to track this metric would be to monitor the amount of training that they undertake and the nature of the sessions.
Covering topics, such as your policy on shadow IT, will help to increase their awareness of cybersecurity matters.

Why is it difficult to measure cybersecurity?
There are a number of reasons why it is not always straightforward to measure cybersecurity. These include:
- There is a lack of a standardized method of measuring and reporting cybersecurity.
- Just because we know how many attacks we stopped doesn’t tell us how many other threats are out there. There is no way to know.
- There is limited visibility on remote workers and their devices and programs that connect to our systems.
FAQ
How often should businesses track their cybersecurity KPIs?
The frequency of tracking cybersecurity KPIs depends on the specific metric being tracked and the needs of the business. Some KPIs may be tracked daily or weekly, while others may only need to be tracked on a monthly or quarterly basis. It is important for businesses to establish a regular tracking schedule that works for their specific needs and goals.
What are some challenges businesses may face when tracking cybersecurity KPIs?
Some challenges that businesses may face when tracking Cybersecurity KPIs include data collection and analysis, selecting the right KPIs to track, and ensuring that KPIs are aligned with the organization’s goals and objectives.
In addition, businesses may face challenges in obtaining accurate and timely data, as well as interpreting the results of the KPIs, and taking appropriate actions based on the findings.
How can businesses use cybersecurity KPIs to improve their cybersecurity posture?
By tracking cybersecurity KPIs, businesses can identify areas where they may be vulnerable to cyber threats and take steps to improve their security controls.
For example, if a business tracks its patch time lag KPI and finds that it takes too long to apply security patches, it may decide to implement a more efficient patch management process.
Similarly, if a business tracks its employee security awareness KPI and finds that employees are not completing cybersecurity training, it may decide to implement mandatory training programs to improve employee awareness and reduce the risk of security incidents.
Are there any drawbacks to tracking cybersecurity KPIs?
While tracking cybersecurity KPIs can provide valuable insights into the effectiveness of a business’s cybersecurity program, there are potential drawbacks to consider. For example, businesses may become overly focused on meeting KPI targets at the expense of other important security considerations. In addition, tracking KPIs may require significant time and resources, and businesses may need to prioritize which KPIs to track based on their available resources.
How can businesses ensure the accuracy and reliability of their cybersecurity KPIs?
To ensure the accuracy and reliability of cybersecurity KPIs, businesses should establish clear data collection and analysis processes. This may involve implementing automated tools and technologies to collect and analyze data, as well as establishing clear data quality standards and data governance processes.
Businesses should also regularly review and validate their KPIs to ensure that they remain relevant and effective in measuring the success of their cybersecurity efforts.
Conclusion
Understanding how your organization works to prevent and mitigate cyber threats is essential to securing your network and reducing attacks and downtime. We hope these cybersecurity KPIs and examples will help you gain an overview of how effective you are at managing security issues and protecting your business.
Vaultry is a tool that scans your network and alerts you to the presence of shadow IT, cracked or out-of-date programs, and other items that create a vulnerability in your organization. It alerts you and allows you to deal with the problem straight away, avoiding costly attacks. Get started with Vaultry today.

